IT security audits are stressful. Not only do they increase your workload, but there’s also a lot riding on them. If you fail, your organization could face fines, additional oversight from the regulator or a loss of accreditations.
Centralized log management helps ease this process by ensuring you can quickly and easily evidence activity across your networks.
But good log data is only as good as the processes and software that underpin it, so it’s important to know how to create a robust strategy and choose the right tools.
This article explains how to use log management for compliance. We’ll cover:
- The role log management plays in compliance
- The challenges involved
- How to use centralized log management in your compliance efforts
- What makes a log management tool suitable for compliance
First, let’s briefly remind ourselves what we mean by IT compliance.
What Is IT Compliance?
IT compliance involves ensuring your technology systems, processes, and data handling practices meet the legal, regulatory, and contractual requirements relevant to your industry.
For many businesses, failing to comply with even one rule can result in fines, legal action, or loss of accreditation.
But compliance isn’t just about avoiding penalties. It’s about building trust with customers and partners, improving security posture, and maintaining operational transparency.
Security vs. compliance: What’s the difference?
→ Compliance focuses on meeting external requirements.
→ Security is about actively protecting your data, systems, and people from threats.
Check out our article on compliance vs security to learn more.
IT requirements are often defined by regulatory frameworks such as:
- General Data Protection Regulations (GDPR): This regulation requires strict data privacy controls for handling personal data of EU residents.
- The Health Insurance Portability and Accountability Act (HIPAA): Regulates how healthcare providers secure patient health information.
- The Network and Information Security Directive (NIS2) is an EU cybersecurity directive that sets rules for protecting critical infrastructure and essential services from cyber threats.
- The Digital Operational Resilience Act (DORA) is a European regulation aimed at strengthening the financial sector’s ability to withstand and recover from ICT-related disruptions.
Some regulations focus on data privacy, others prioritize security controls or audit transparency. But most require a combination of data protection, access controls, and collecting auditable data.
All of these requirements depend on reliable, well-managed log data, which is why log management is critical to IT compliance.
What Role Does Log Management Play in Compliance?

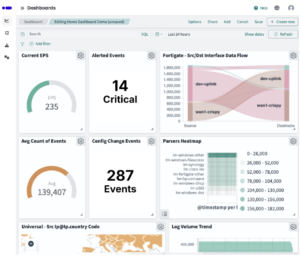
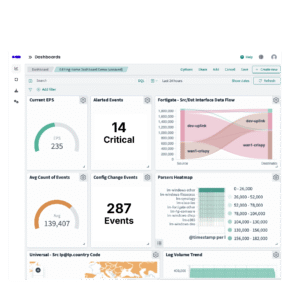
Log management is the process of collecting, storing, organizing, and making searchable the event logs generated by your systems, applications, and infrastructure.
It helps centralize log data so you can monitor activity, detect issues, identify their root causes, and meet regulatory requirements. Moreoever, log management provides the visibility and evidence needed to show regulators and your own internal teams that systems are behaving as expected, sensitive data is protected, and unauthorized activity is being detected and addressed.
At a minimum, most regulations stipulate requirements specifically related to log management, including:
- Recording user activity and system changes
- Retaining those logs for a defined period
- Preventing logs from being tampered with or deleted
- Restricting access to logs based on job role
- Being able to produce records during an audit or investigation
For instance, during a GDPR investigation, a company may be asked to provide detailed logs showing who accessed personal customer data and when. Without a centralized and searchable log archive, retrieving this information quickly can be nearly impossible.
Good log management strategies and software help you meet these requirements and give you confidence that no critical security events are slipping through the cracks.
It also supports more advanced security monitoring tools, such as security information and event management (SIEM) platforms, which rely on consistent, high-quality log data to detect security threats and enforce policy.
Common Pitfalls and How to Avoid Them
Many organizations run into compliance issues due to poor log management practices.
Fixing these issues costs time and money. Worse, it could result in a regulatory fine or a security breach, putting your reputation, data and system integrity at risk.
Here are some common compliance mistakes IT teams make:
Collecting the wrong data
Compliance frameworks often require specific types of log data, such as:
- User activity
- Access attempts
- System changes
Many businesses underestimate the value of log management for compliance until they face their first regulatory audit. Failing to collect the right security logs will result in gaps in your audit trail, making it difficult to prove compliance or investigate incidents.
Not securing your log data
Log files can contain sensitive information, including user credentials, access tokens, or IP addresses. If logs aren’t encrypted or access-controlled, you risk a data breach, which could result in regulatory action against your company.
Inconsistent retention policies
Most businesses are subject to multiple regulations, and each one may have different rules for how long logs must be kept. The challenge isn’t just knowing the requirements, it’s ensuring your systems enforce each one correctly.
That means setting retention rules by log type or data category, not using a one-size-fits-all policy.
Storing logs without reviewing them
Simply keeping logs isn’t enough. Potential compliance violations or security issues can go unnoticed without regular review and log analysis.
For example, unusual login patterns or unauthorized data transfer may only be visible through analysis and correlation over time.
Best Practices for Implementing Log Management for Compliance

1. Map your compliance requirements to your systems
Start by identifying which regulations apply to your business (e.g., PCI DSS, HIPAA, GDPR) and what types of log data each one requires. Map those requirements to the specific systems in your environment, from servers and endpoints to cloud services and third-party platforms.
2. Set up consistent, centralized log collection
Centralized log collection involves ensuring all critical infrastructure, applications, and services are connected to your log management platform. Collect logs in a consistent format and route them to a central location to simplify storage, analysis, and reporting.
3. Apply retention rules based on compliance needs
Create automated retention policies for each log type, based on the applicable regulations. Use your log management platform to enforce those rules, so nothing is deleted too early or kept longer than necessary.
For example, fintech firms are subject to PCI DSS regulations, which stipulate they must retain logs for at least one year, and ensure log data is immediately accessible for at least 90 days.
Their centralized log management solution could enforce this automatically by deleting outdated logs and archiving the rest. This would reduce manual error and storage costs.
4. Restrict access using role-based controls
Limit who can view or manage log data. Implement role-based access control (RBAC) to ensure that only authorized personnel have access, and log every access event to maintain auditability.
5. Schedule regular reviews of log coverage
Periodically audit your environment to ensure all relevant systems are logging correctly. This is especially important after onboarding new tools or infrastructure changes.
6. Automate continuous monitoring and alerting
Set up alerts for policy violations, suspicious activity, and failed login attempts. Use SIEM integrations or built-in alerting to identify issues early and respond faster.
7. Document your policy and processes
Keep a written log management policy that outlines:
- What data is collected
- Why it’s collected
- How long it’s stored
- Who is responsible for maintaining it
This documentation is key for internal training and external audit reports.
How to Choose a Log Management Tool for Compliance

If your goal is regulatory compliance and not just monitoring system behavior, your log management platform needs to go beyond basic data collection.
It needs to support strict security, retention, and reporting requirements. It must help you meet specific legal requirements, produce reliable evidence for audits, and keep pace as your infrastructure grows or regulations evolve.
Here’s what to look for, and why it matters.
1. Supports broad log source coverage
To stay compliant, your log management tool must be able to collect logs from all relevant parts of your infrastructure, including servers, cloud services, endpoints, applications, and third-party tools.
Many compliance issues stem from blind spots: in other words, the system generates a log, but it isn’t captured or monitored.
The tool should make it easy to confirm that all expected log sources are connected and actively sending data and alert you if any source stops sending logs or drops below a baseline volume.
When choosing a platform, check whether it:
- Has native integrations for your existing tech stack (firewalls, servers, security devices, etc.)
- Can handle custom log sources without complex workarounds
- Supports both real-time ingestion and batch uploads
2. Offers strong controls for log integrity and access
Security and privacy regulations require logs to be stored in a tamper-proof, access-controlled environment.
In an audit, you’ll need to prove that logs haven’t been altered and that only authorized users could access them. Your log management tool must make this easy to configure and enforce.
Ask yourself:
- Does it support encryption at rest and in transit?
- Are access permissions role-based, and can they be tightly scoped?
- Is there an immutable storage option (e.g. WORM)?
- Can you view a full audit trail of who accessed what, and when?
3. Enables flexible, regulation-aligned retention policies
A good tool should let you set different retention periods depending on regulation, log type, or system, and automatically delete or archive logs when they reach the end of their required lifespan.
If the tool only allows global retention settings or requires manual intervention, you’re likely to run into compliance issues.
Find out:
- Can retention policies be applied at a granular level?
- Is deletion or archiving automated?
- Can logs be flagged for legal hold or extended retention?
4. Provides audit-ready search and reporting
When auditors request data, your tool should make it fast and easy to deliver.
Some tools offer built-in compliance dashboards for frameworks like PCI DSS or GDPR, which can save significant time during reviews.
Evaluate:
- How quickly can you retrieve logs based on user, system, or timeframe?
- Can the tool generate reports that align with compliance frameworks?
- Are logs exportable in industry-standard formats?
5. Integrates well with your existing tech stack
Compliance requires consistency across all layers of your environment, which often involve multiple systems, tools, and logging formats. This makes it harder to maintain consistent retention, access control, and visibility.
Poor integration leads to missed logs, extra manual effort, and inconsistent compliance coverage.
Your log management tool needs to unify sources from across your environment to avoid compliance gaps.
Check:
- Does it integrate with your SIEM or threat detection platform?
- Does it work with your cloud providers’ native logging (e.g. AWS CloudTrail)?
- Can it ingest logs from CI/CD tools and container platforms?
6. Scales with your data and regulatory complexity
As your infrastructure grows, so will your log volume and your regulatory exposure. Your tool needs to scale without sacrificing performance or driving up costs unpredictably.
Ask:
- What’s the pricing model? By volume, host, retention?
- Is ingestion throttled or capped at higher volumes?
Selecting a Log Management for Compliance: Quick Evaluation Checklist
Before committing to a platform, ask:
✅ Can it collect logs from every system we use (including cloud and third-party)?
✅ Does it support encryption, access control, and immutable storage?
✅ Can we apply different retention policies for different log types?
✅ Are audit logs exportable and easy to filter?
✅ Does it integrate with our SIEM, DevOps, and cloud stack?
✅ Will it scale as our infrastructure and compliance obligations grow?
Log Management Software: The Foundation of Your Compliance Programs
Compliance requirements are getting more complex all the time. And without the right systems in place, log data quickly becomes a liability instead of an asset.
Choosing the right tool for log management for compliance can save your team time and reduce the risk of audit failures. It will help you enforce retention policies, secure sensitive data, provide clear audit trails, and integrate across your infrastructure without adding unnecessary complexity.
Logmanager is built to do that. It’s a compliance-ready log management platform that helps IT and security teams meet regulations, no matter how complex the environment.
Find out how Logmanager can simplify your compliance efforts and secure your logs at scale. Book a showcase demo today or start your 7-day free trial.