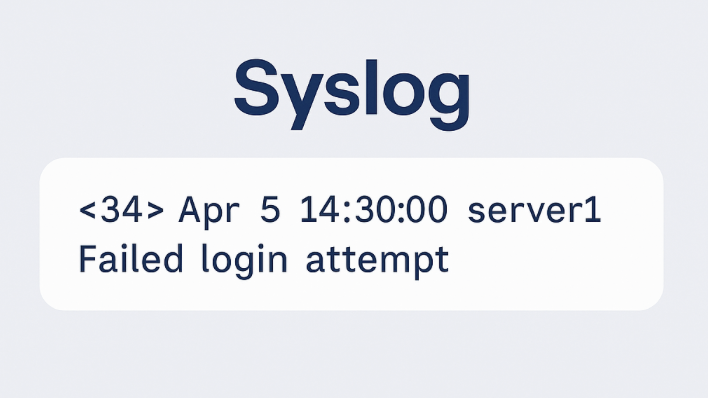
The syslog format is one of the most widely used reporting standards in the IT industry. It’s a core method for capturing and sharing log data across servers, firewalls, and network devices.
However, the syslog system is limited on its own. It lacks structure, offers no built-in security, and can be difficult to work with at scale.
To get real value from it, you need tools that can enhance and enrich syslog, making it consistent, searchable, and useful for modern security and operations teams.
In this article, we’ll explain what the syslog message format is, where it works well (and where it doesn’t), and how Logmanager builds on syslog to deliver powerful observability, threat detection, and compliance across your infrastructure.
What Is the Syslog Format?
The syslog format is a system used to store and send log messages across networked systems.
It is a widely adopted set of rules or specifications that enable different systems or technologies to communicate or operate together.
It has been around since the 1980s and is foundational to how components, such as servers, routers, and firewalls, communicate system events.
Syslog standards were recently updated in RFC 5424 by the Internet Engineering Task Force, an international community of network designers, engineers, and researchers that develops and promotes voluntary technical standards to keep the Internet running smoothly.
One of the reasons syslog has been widely adopted is that its simplicity makes it incredibly flexible.
But this is both a strength and a weakness; devices can implement it differently, and the message body is often unstructured.
Despite these drawbacks, the syslog format remains the backbone of log transmission in networks. It’s easy to implement, supported by nearly all networked devices, and enables central collection of critical events, making it essential for system monitoring, troubleshooting, and security visibility.
What does a syslog message look like?
The syslog message format follows a simple structure and is made up of several parts:
- Priority value (PRI): A numeric value that combines the facility (source of the message) and severity (level of urgency).
- Header: This typically includes a timestamp and hostname or IP address.
- Message (MSG): The body of the log, usually free text describing the event.
Here’s an example syslog message that explains a failed login attempt via SSH:
pgsql
Copy
Edit
<34>Oct 11 22:14:15 webserver01 sshd[12345]: Failed password for invalid user admin from 192.168.1.100 port 54875 ssh2
In this example:
- <34> is the message priority
- Oct 11 22:14:15 is the timestamp
- webserver01 is the hostname
Syslog format messages are often transmitted using User Datagram Protocol (UDP) protocol. UDP is fast and lightweight, but not very secure, and doesn’t guarantee reliable delivery.
Because of this, many modern IT teams choose to override UDP in favor of:
- Transmission Control Protocol (TCP): More reliable but adds overhead.
- Transport Layer Security (TLS): Encrypts the data, offering both security and reliability.
This is especially true for companies where logs are critical for security or compliance.
Where Syslog Is Commonly Used
Syslog format is widely used across IT infrastructure because it’s lightweight, easy to implement, and supported by nearly every major network and Unix-based system.
You’ll most often find it in environments where consistent, low-overhead logging is essential.
It is commonly used to centralize logs from multiple sources into a single monitoring or SIEM platform, allowing IT teams to correlate and investigate activity across the entire environment.
Typical sources of syslog messages include:
- Linux and Unix servers
These systems use syslog to report system activity, authentication attempts, scheduled tasks, and kernel messages.
- Network devices
Firewalls, routers, switches, and load balancers from vendors like Cisco, Juniper, and Fortinet send messages to report on traffic, configuration changes, and security alerts.
- Security appliances
Intrusion detection systems (IDS), VPN gateways, antivirus gateways, network access control, identity management solutions like AD, LDAP, and others often rely on syslog to export event logs to a central system.
- Appliances and embedded systems
Many printers, IP cameras, and NAS devices emit syslog format as their default message logging method due to its low resource demands.
How Syslog Compares to Other Message Formats
Syslog isn’t the only logging format used in modern environments, and in many cases, it’s not the most suitable.
That’s because although it’s widely supported, syslog format is relatively unstructured as any vendor creates their own structure of the freeform message field. Most modern formats aim to improve on that by offering consistency, clarity, and better support for automation.
Below are some of the most common alternatives and how they compare to syslog.
JSON
JavaScript Object Notation (JSON) consists of a pair comprising a key, such as “user” and “ip” and a value, which would be the actual username and the IP address, respectively.
It’s commonly used by applications, APIs, and cloud-native platforms because it’s both human-readable and makes message parsing easier.
JSON allows key fields to be clearly defined and, therefore, extracted. This makes it more suited to automated analysis than syslog, which typically logs messages as free text.
Windows Event Logs
Windows systems don’t use the syslog format natively. Instead, they generate logs in a proprietary binary format managed by the operating system.
These logs require specific tools or agents to read. To centralize Windows logs alongside syslog, organizations often use log collectors that convert them into syslog or another standard format.
CEF and LEEF
Common Event Format (CEF) and Log Event Extended Format (LEEF) are formats designed to record security events.
They include predefined fields for items such as source IP, username, and event type, making them easier to parse and correlate in SIEM platforms. Both are often transmitted within a syslog message, combining the ubiquity of syslog with more structure in the message body.
Key Limitations of the Syslog Format
While syslog is widely supported and simple to implement, it has several technical limitations that can make it difficult to work with in large or security-focused environments.
These issues don’t mean syslog should be avoided, but they do explain why additional tools may be needed to make it usable at scale.
Unreliable delivery over UDP
Syslog commonly uses UDP as its transport protocol. While fast and low-overhead, UDP doesn’t guarantee message delivery, ordering, or integrity.
If a log message is lost in transit, there’s no retry or confirmation, and the loss often goes unnoticed.
If you are using syslog for critical events where data loss isn’t acceptable, then you’ll need to use TCP that can even be encrypted using TLS, ideally version 1.2 and higher. However, these protocols negate some of the speed and simplicity benefits gained from using syslog.
Lack of consistent structure
Syslog format messages typically contain a priority, timestamp, hostname, and a free-text message body.
The message itself is unstructured, meaning each vendor or device can format it however they like. For example, two firewalls may log the same event using completely different wording.
This inconsistency makes it hard to search, filter, or correlate syslog data without additional processing.
No built-in metadata or context
Unlike structured formats like JSON or CEF, syslog messages don’t support key-value fields by default.
There’s no standard way to include user IDs, geolocation data, or event types. This makes it harder to perform automated analysis or threat detection without enriching the data later.
Timezone and timestamp inconsistencies
Older syslog standards like RFC 3164 don’t include any support for timezone information in timestamps. The format only records the month, day, and local time, without indicating the time zone or year.
This can lead to confusion when aggregating logs from systems in different regions, making it harder to reconstruct timelines accurately during investigations.
No native security features
The pre-2009 version of syslog doesn’t include any built-in security features. Syslog messages are plain text with no encryption, no way to verify the sender, and no protection against tampering.
Unless you use an additional secure transport like TLS over TCP, syslog traffic can be intercepted, faked, or modified in transit; a serious risk for environments handling sensitive data.
Device-level setup and blind spots
Syslog must be configured on each device individually, and if something breaks (like a typo in the destination IP), event messages silently fail to be sent. Unless you’re actively monitoring ingestion, these blind spots can go unnoticed for weeks.
Use the Right Tools to Enhance Syslog Data
You get the idea: Syslog is simple, widely supported, and still heavily used. But it wasn’t built for modern security, compliance, or large-scale environments.
On its own, it lacks structure, offers no built-in security, and can be difficult to search or correlate with other log file types.
To get value from syslog, you need a tool that can handle its limitations, extract useful information, and put it into context. A good example of this is Logmanager.
Logmanager is a centralized log management and SIEM platform that helps organizations collect, parse, enrich, and analyze logs from across their infrastructure.
It fully supports syslog and extends its capabilities, making even basic device logs structured, searchable, and actionable.
Here are some of the ways it enhances syslog:
Secure transport with full support for TCP and TLS
Logmanager supports syslog ingestion over TCP and TLS, ensuring reliable message delivery and encrypted transport. This protects sensitive log data in transit and prevents silent data loss.
Auto-parsing and normalization of diverse syslog sources
Logmanager transforms raw, unstructured messages into clean, consistent fields, enabling precise search, filtering, and rule-based alerting across mixed infrastructure.
It does this by automatically detecting and parsing varied formats using built-in rules and normalization processes.
Enrichment with context to unlock insight
On their own, syslog messages lack useful context. This is where the centralized log management tools such as Logmanager comes in, making each event more meaningful by enriching it with additional data, such as geolocation, user identity, asset tags, threat intelligence information or other custom defined datasets.
This transforms vague incoming log messages like “connection denied” into events you can confidently interpret and act on.
Correlated search across all log file sources
Logmanager doesn’t just collect syslog; it ingests logs from cloud services, applications, Windows systems, and more.
This means you can correlate syslog events with data from other parts of your environment. For example, matching a failed login on a VPN with a successful login in Microsoft 365 could reveal a compromised account.
Health monitoring and delivery diagnostics
If a source stops transmitting syslog messages, you might not notice, especially over UDP. Logmanager includes input monitoring to detect ingestion issues, sends notification messages on missing data, and ensures every critical device is still reporting. That means fewer blind spots and more reliable data.
Cost-effective storage and retention
Syslog traffic can grow rapidly. Logmanager supports tiered storage, compression, and retention policies that help manage this volume efficiently. You can keep critical logs searchable for as long as needed, while archiving less important data to save on cost.
Dashboards, alerts, and visual search
Traditional syslog setups don’t offer visual tools. Logmanager includes intuitive dashboards, configurable alerts, and rich search functionality, allowing teams to investigate issues, monitor trends, and respond quickly without having to sift through raw log lines.
Logmanager: Make Syslog Useful

Syslog might be simple, but using it effectively is anything but. Its lack of structure, security, and consistency makes it difficult to manage at scale, particularly when relying on it for incident detection, compliance, or system monitoring.
Logmanager transforms raw syslog data into something far more powerful. It adds structure where there is none, enriches logs with context, secures transmission, and makes everything searchable, visual, and actionable. That means fewer blind spots, faster investigations, and better decision-making.
If you’re still relying on basic syslog collection or struggling to make sense of the data you already have, it’s time to see what Logmanager can do.
Sign up for a free trial or request a demo to find out how Logmanager can help you get more out of your logs.