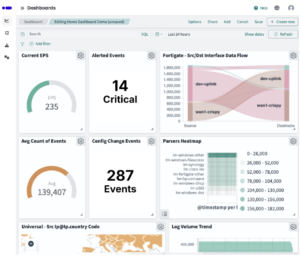
Introducing Logmanager 4: Better Performance and a Streamlined UI
Logmanager 4.1.0 marks a fundamental shift in our platform architecture to deliver a more sustainable, higher performance and more secure foundation for your data.

Logmanager 4.1.0 marks a fundamental shift in our platform architecture to deliver a more sustainable, higher performance and more secure foundation for your data.
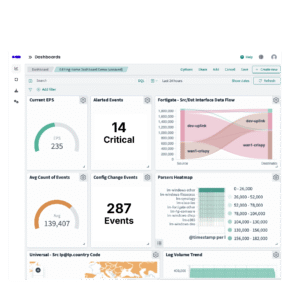
After doubling its revenue in two years, the company sees the new release as a key pillar of its mission to bring customers worldwide a log management solution without the enterprise overhead.
Learn how log aggregation tools work, what to look for, and which platforms are best suited to different technical needs in a business environment.

The syslog format is one of the most widely used reporting standards in the IT industry. In this article, we’ll explain what the syslog message format is, where it works well (and where it doesn’t).

In this expert blog, we take a deeper dive into the importance of log management for compliance, highlight common pitfalls, and explain what a log management tool should offer to help meet regulatory requirements.

Explore 8 log file analysis tools, from simple viewers to advanced options, to help you monitor log data, troubleshoot, and optimize your systems effectively.

Log management appears to be a vital component of DORA compliance. But how exactly does it contribute? In this article, we break down key parts of the DORA regulation to show where and how log management plays a critical role in meeting its requirements.

Discover the core types of log files, their sources, and what data to capture to support effective incident detection, investigation, and IT compliance.

What is log analysis? This article summarizes its critical role in managing and maintaining critical networks.

Explore the key components of effective log management and best practices to help you turn raw data into valuable security and operational insights.