- Define the scope of log management
Conduct a full inventory of your infrastructure to determine which systems, applications, and services should be included in log management.
- Identify key areas of interest
Decide which activities need to be logged and set the appropriate level of monitoring for each. Prioritize events that are critical for security, compliance, and troubleshooting.
- Structure logs for better search and accessibility
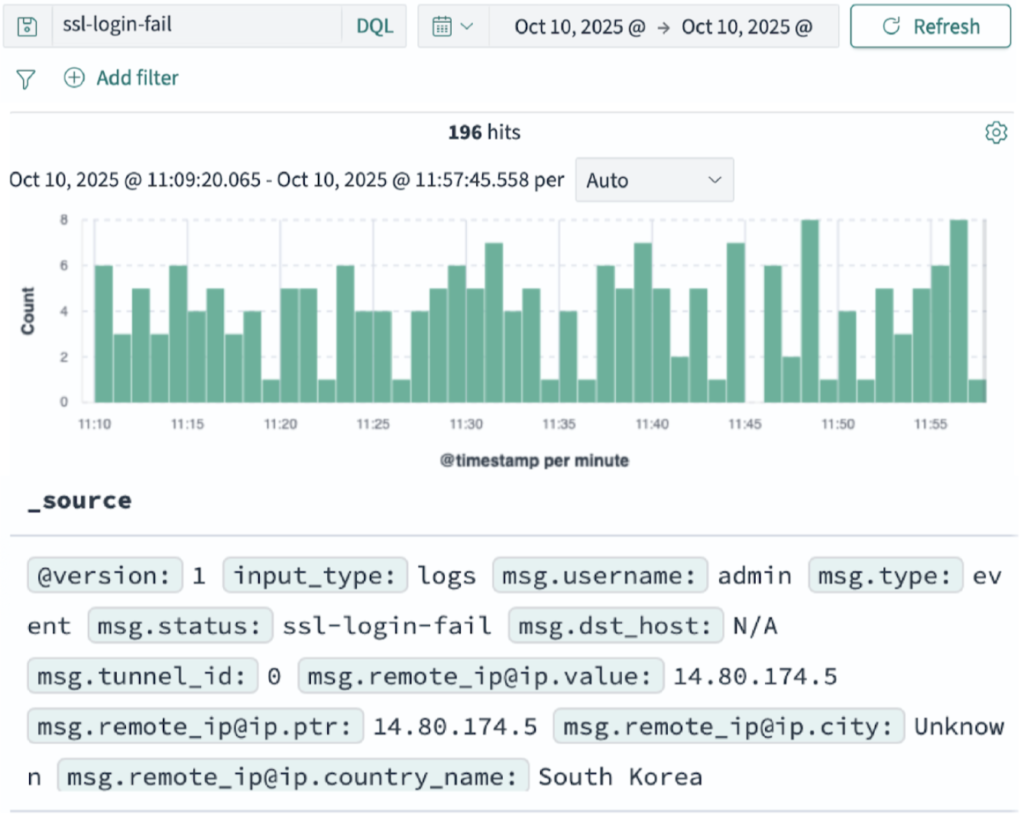
Logs come from a wide variety of sources ( applications, databases, network devices, cloud services, and security tools) each with its own format. To store them in a unified format on a central log server, they must first be parsed (read and restructured). Parsing ensures logs are normalized and easy to search.
- Use log indexing and tagging
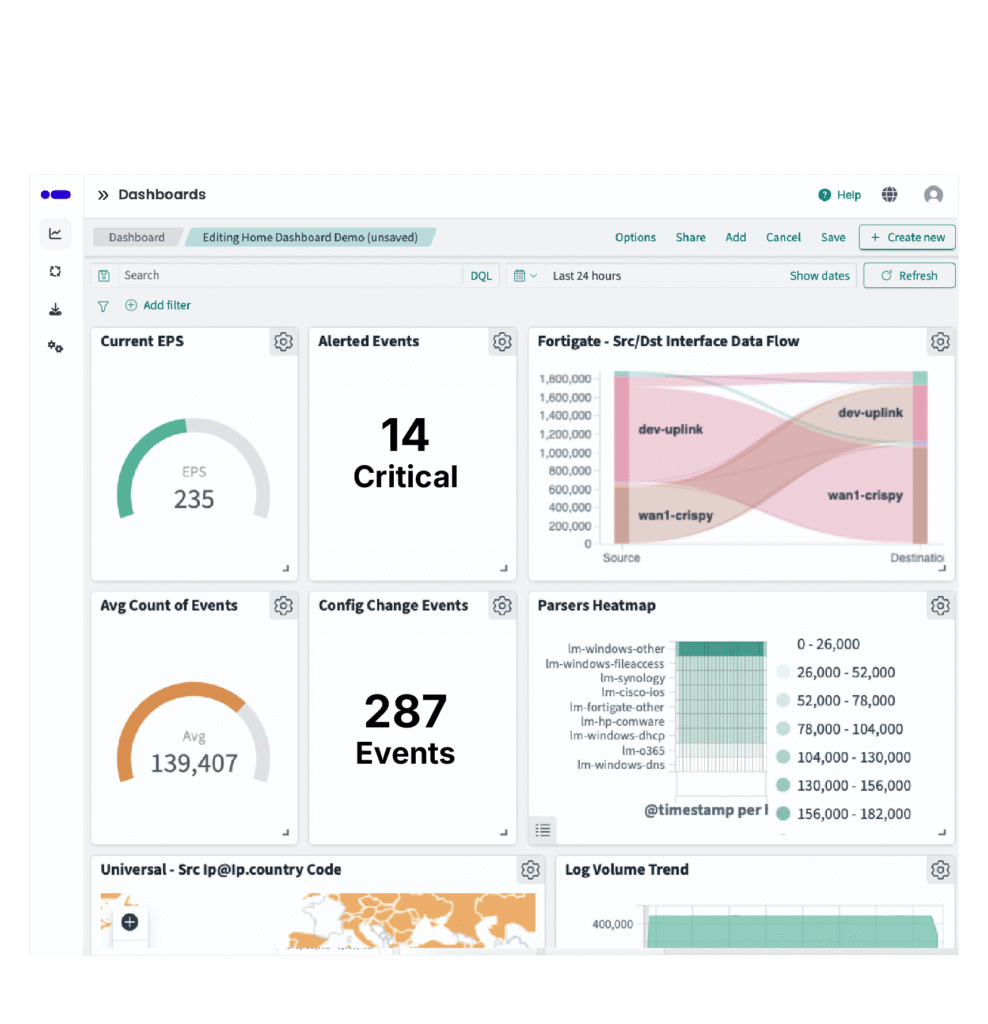
Indexing and tagging logs significantly improve observability, simplify troubleshooting, and make it easier to correlate events across different systems.
- Centralize logs for visibility
Bringing logs into a single location through centralized log management software reduces manual effort, enables faster investigation of security incidents or failures, and provides a complete view of your environment.
- Set up alerts
Automated alerts for critical events ensure a rapid response to potential threats or system issues, minimizing downtime and risk.
- Test and validate regularly
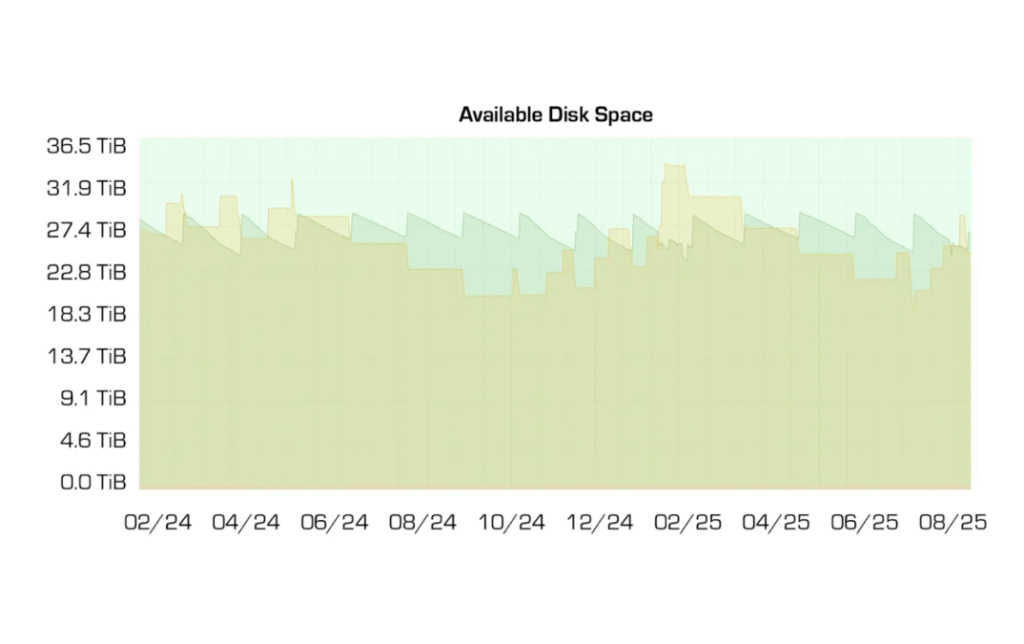
Regularly test your logging setup to ensure logs are being captured, stored, and analyzed correctly. Validation helps identify gaps before they become serious issues.
- Store logs securely with access control
Use immutable storage (tamper-proof environments) to preserve log integrity for a defined retention period or permanently, depending on compliance requirements. Restrict access to authorized personnel only, ideally through Role-Based Access Control (RBAC) or similar access management systems.
Read our article on log management best practices to explore the key differences in depth.